Exploring InsightIDR by Rapid7: A Modern SIEM Solution — Part 2: Architecture

InsightIDR is a hybrid on-premises SaaS tool. It has multiple components so let’s discuss them one by one.
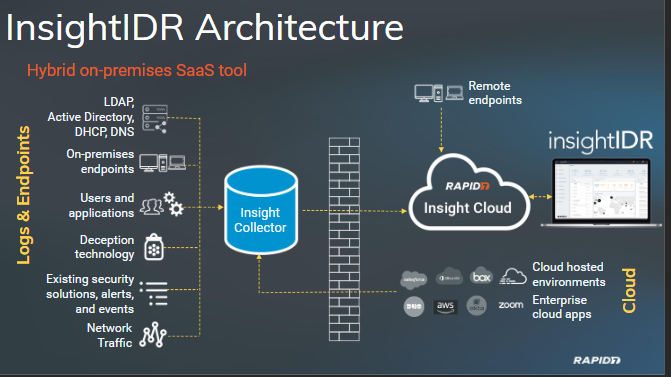
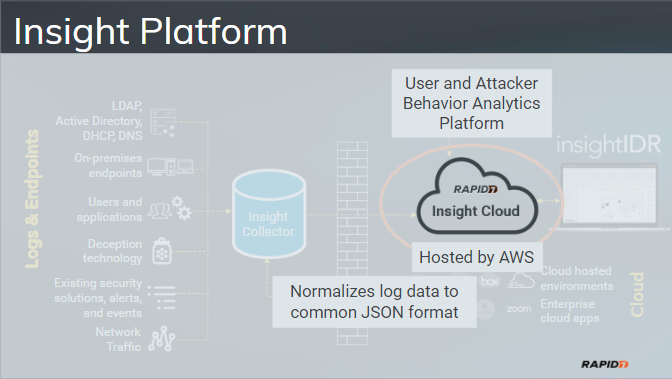
The Section on the left side of the image is called Logs and Endpoints. We would go into the details a bit further.
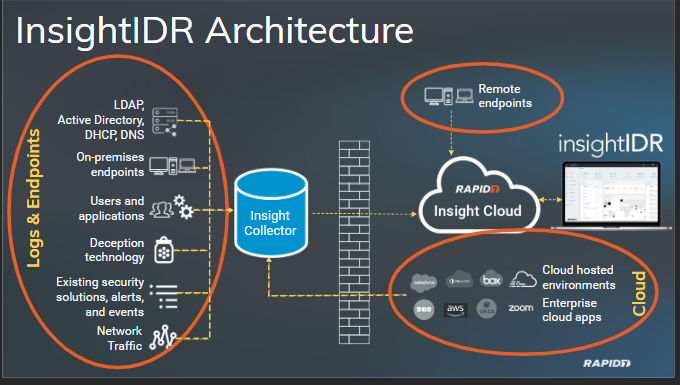
The Data from authentication Logs, Endpoints and network devices is aggegated into the on-premises Data Collector called Insight Collector.
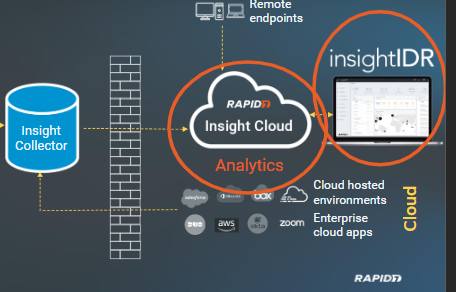
Then from Insight Collector data securely moves to AWS with a Rapid7 InsightIDR Customer databases adn web interfaces are hosted.
InsightIDR then runs analytics on this data to look for normal traffic and also for any IOC (Indicator of compromise).
InsightIDR monitor endpoints using Insight Agent which are installed on endpoints
InsightIDR uses Deception Technology to identify malicious activity. This deception technology include Intruder Trap, honeypots, honey users, honey credentials & honey files.

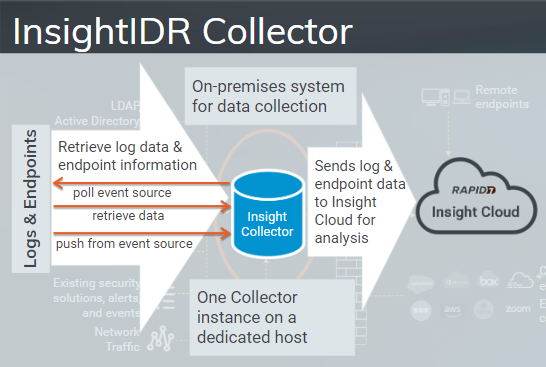
Insight Collector
This retrieve log data and endpoint information. It either poll event sources or retrieve data from event sources. Then the data goes into Insight Collector. It by default removes any duplicates from the data and then send log and endpoint data to InsightIDR cloud for analysis.
Minimum and maximum one collector instance must be present on the dedicated endpoint machine to send logs to Collector.
What is Polling?
Polling, in the context of data retrieval or communication systems, refers to the process of actively querying or checking a source at regular intervals to determine if there is new information available. It’s like repeatedly asking a device or a system, “Do you have any updates or data for me?” This is done to ensure that the system retrieving data stays updated and can capture any changes or new information as soon as it becomes available.
Insight Agent:
This is a lightweight agent installed on the end device to monitor endpoint and report any security related event. It only collectors information about the device it is installed on.
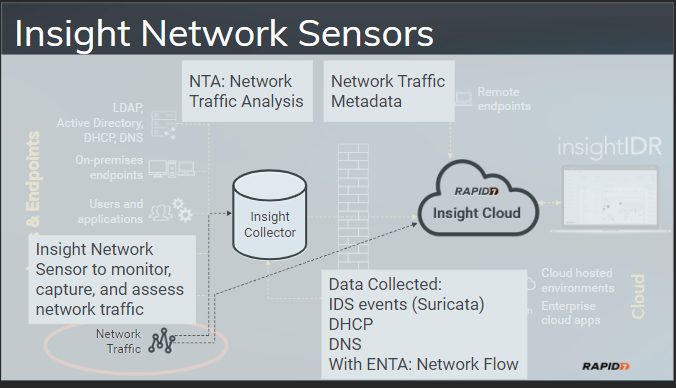
Insight Network Sensor:
This component is used for identifying any malicious activity on the network. Data is collected using suricata from DHCP, DNS and other traffic flowing through the network. With ENTA (Enhanced Network Traffic Analysis) it can view metadata of all the traffic like IP address ,port and protcols being used.
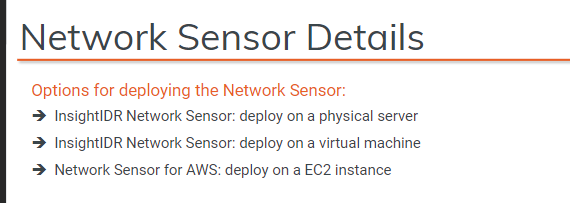
There are 3 ways to deploy network sensor.
Insight Cloud
It is a User and attacker behavior analytics platform. It checks data for any malicious activity or any IOC.